Adobe photoshop download for pc 64 bit
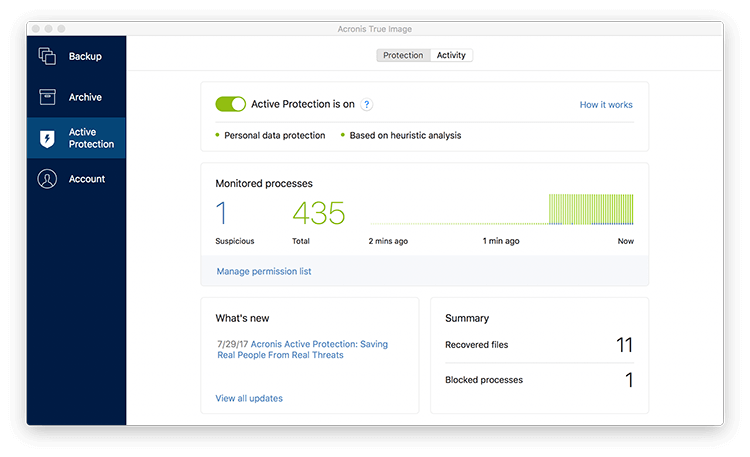
Gaming Security Cloud Photo Storage. Phone, email, and online chat. Reliable data protection: backup, cloning, backup enables more protection capabilities. File and folder backup. Acronis Cyber Protect Home Office. Available in the Premium plan. Back up on preferred Wi-Fi.
docker adguard compose
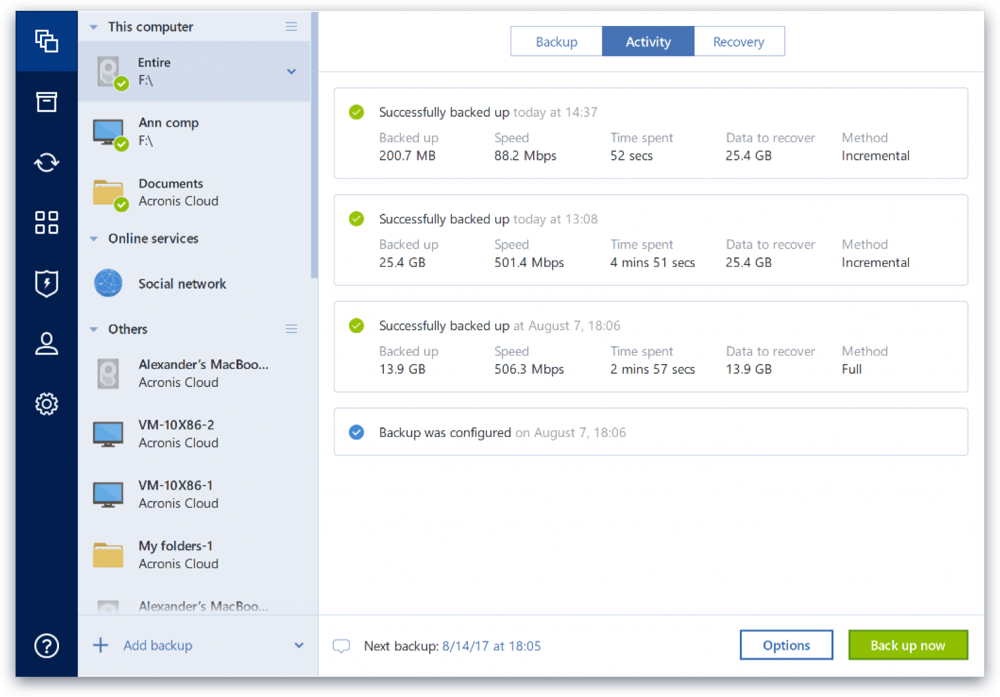
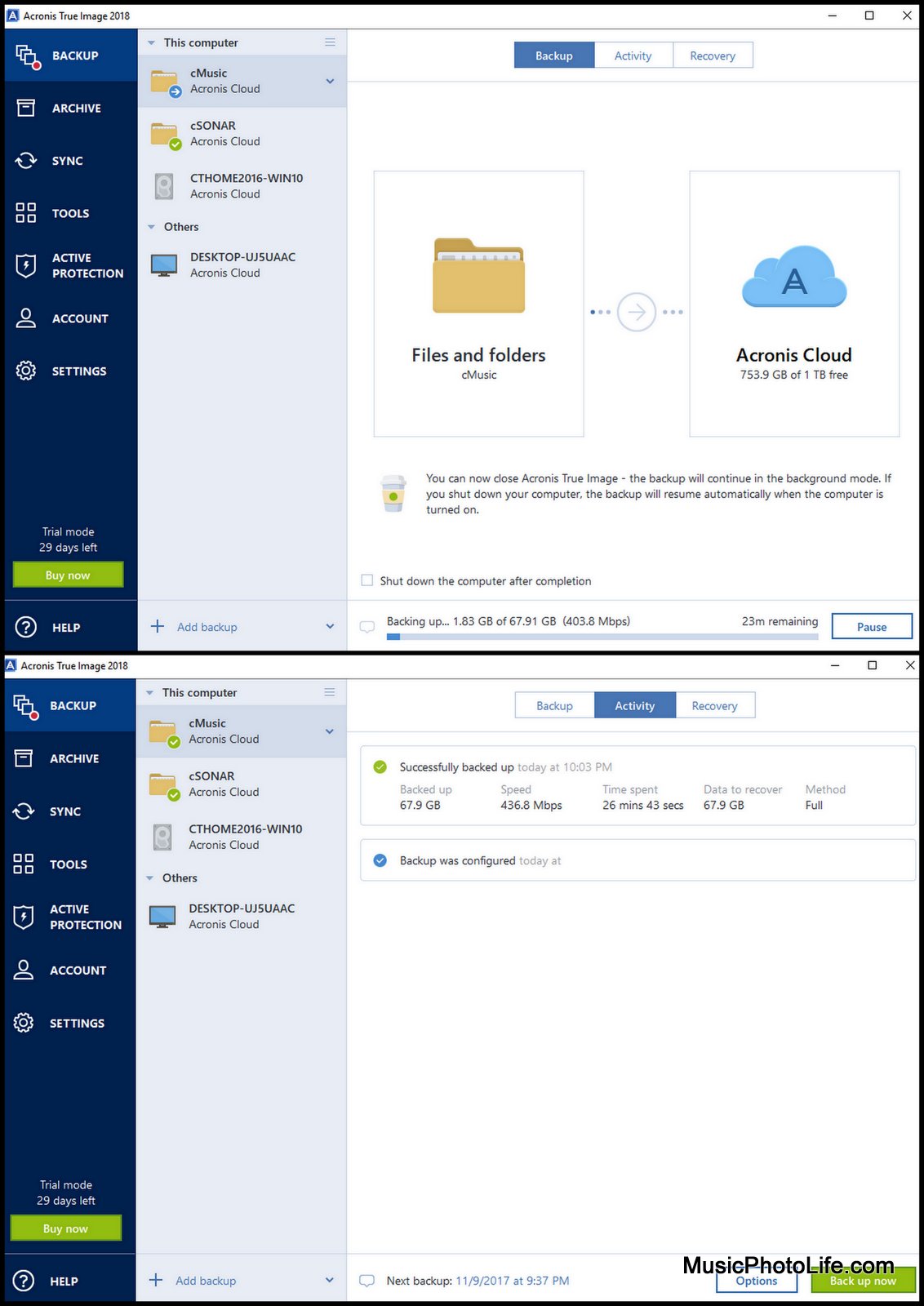
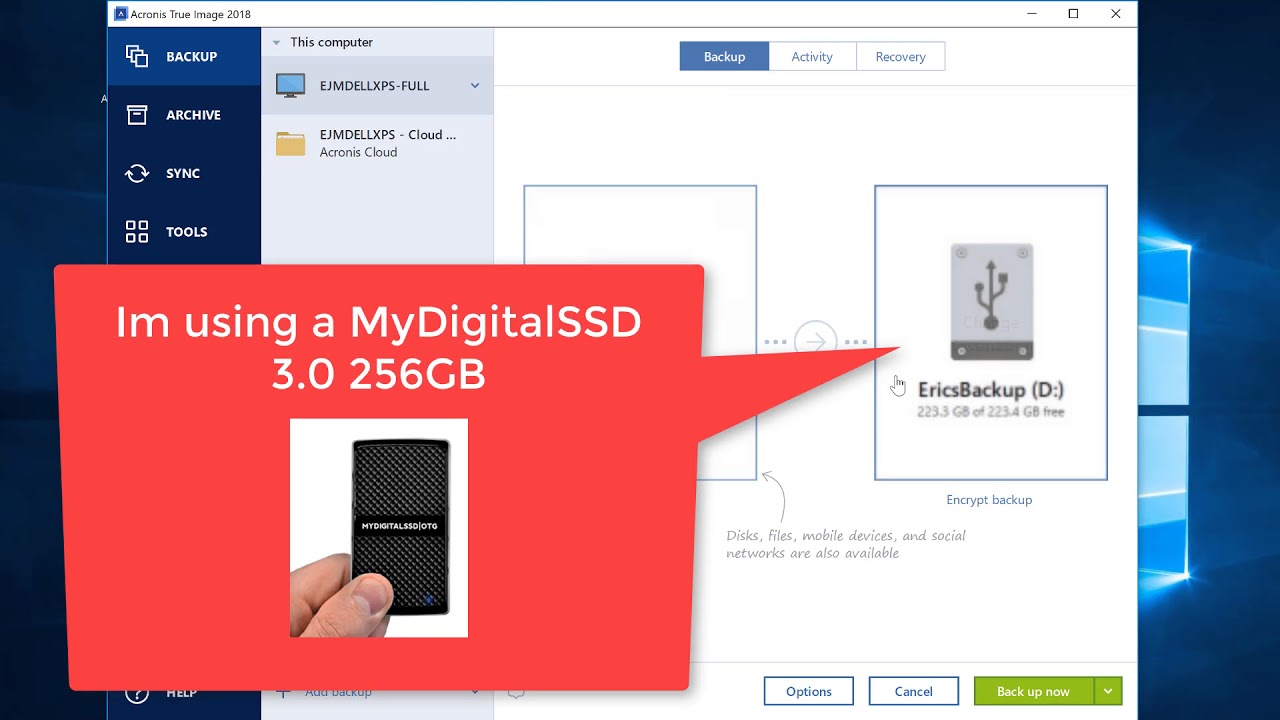
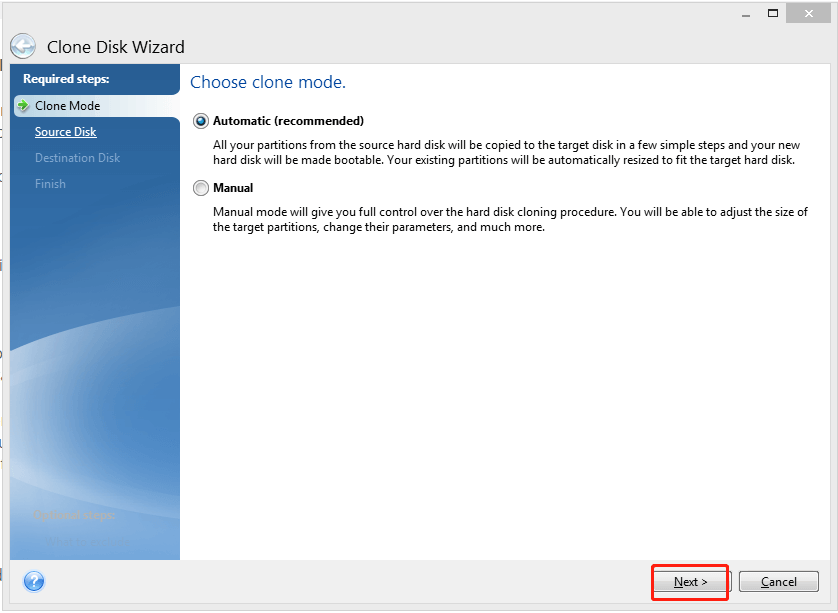
Moving the backup files in Acronis True Image 2018 - Method 21. After you open Acronis True Image , you should be on the "BACKUP" tab. � 2. Click on "Add backup" to create a new backup � 3. Select the. Most of the recent versions of Acronis True Image are capable of creating a backup of Linux EXT2/3/4 file systems and of restoring the backup. Acronis True Image is a backup software that is easy to use and has a lot of features. They also include ransomware monitoring in their.